Evernote has fixed a vulnerability that could have allowed an attacker to run malicious code on a victim’s computer.
Dhiraj Mishra, a security researcher based in Dubai, reported the bug to Evernote on March 17. In a blog post showing his proof-of-concept, Mishra showed TechCrunch that a user only had to click a link masked as a web address, which would open a locally stored app or file unhindered and without warning.
Evernote spokesperson Shelby Busen confirmed the bug had been fixed, and said the company “appreciates” the contributions from security researchers.
The researcher ‘popped calc’ as a way to demonstrate a remote code execution bug in Evernote (Image: supplied)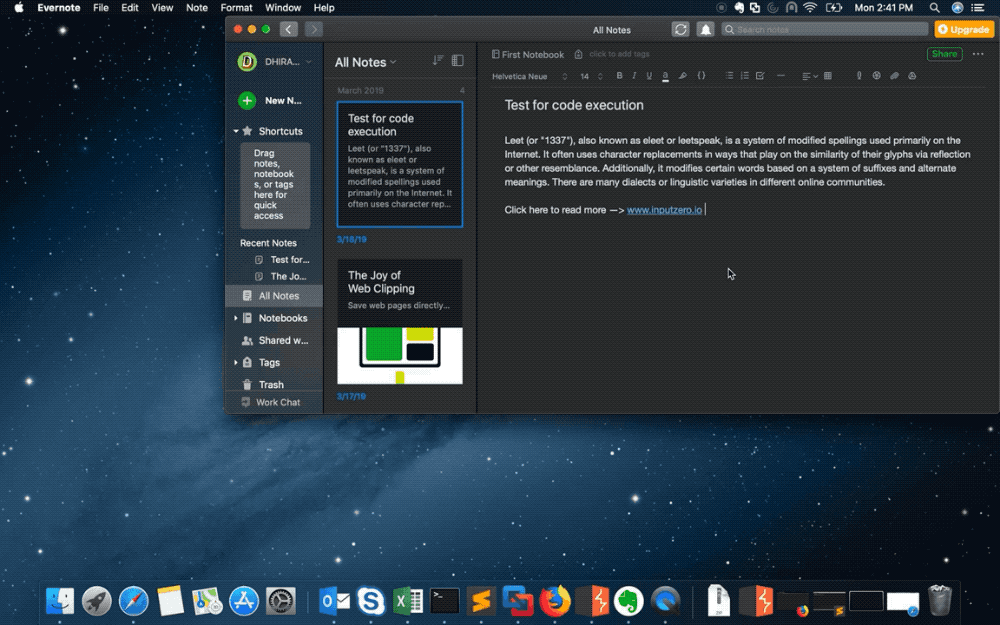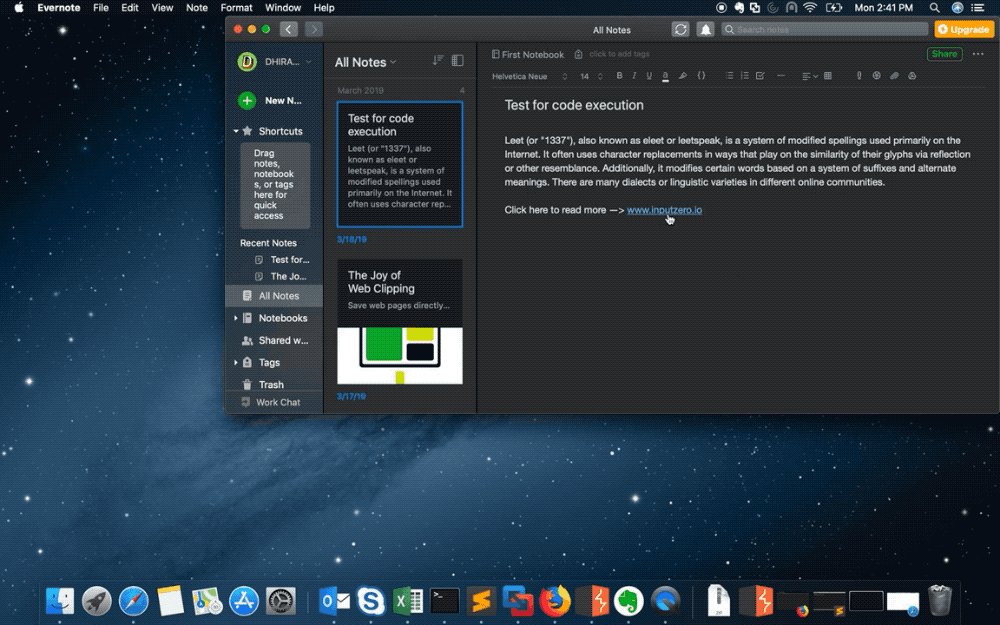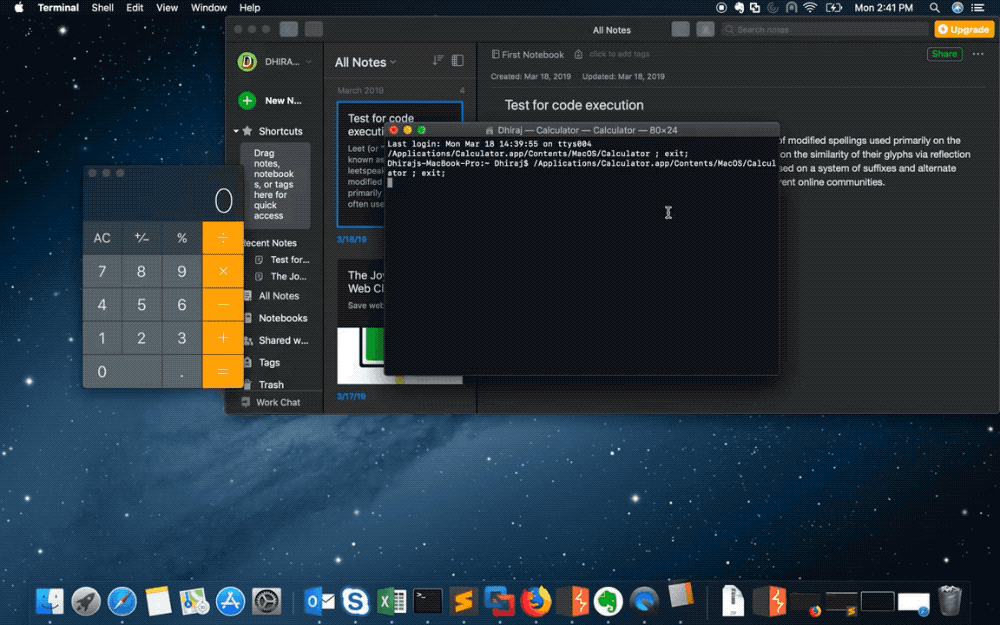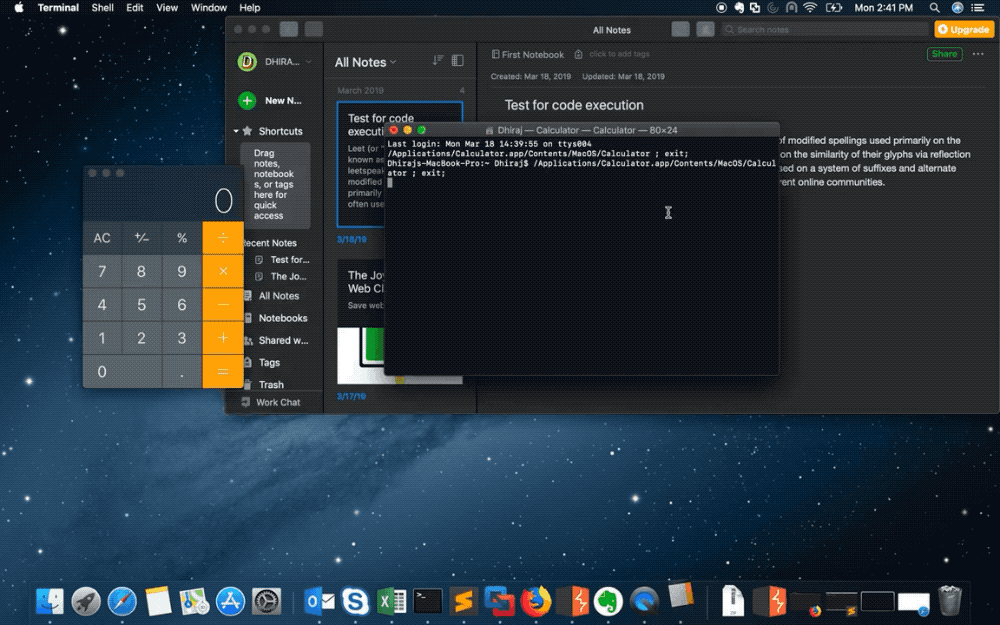
MITRE, the vulnerability database keeper, issued an advisory under CVE-2019-10038.
The bug could allow an attacker to remotely run malicious commands on any macOS computer with Evernote installed. Since the fix went into effect, Evernote now warns users when they click a link that opens a file on their Mac.
A similar local file path traversal bug was revealed Tuesday in Electronic Arts’ Origin gaming client.
Evernote was forced to reset close to 50 million passwords after a breach in 2013, and later caused controversy by changing its privacy policy that allowed employees to access user data. The company later walked back the policy change after user complaints.
Security flaw in EA’s Origin client exposed gamers to hackers
